Overview[]
'Botnet hosting' is a technique used by some spammers in order to host web pages in such a way as to eliminate any links to the spammer (and to save money on hosting fees).
The spammer registers a domain through a registrar and then selects some zombie PCs under his control to act as both web and name servers. The zombie name servers are listed with the registrar as name servers for the domain, so attempts to resolve hosts in the domain will be directed to one of the zombies. The name server software running on the zombie implements a basic 'round-robin' algorithm, so that a request to resolve a host in the domain will return the IP address of one of the zombies. Web pages will then be served from that zombie.
Advantages for the spammer[]
Hosting on zombies instead of a virtual host leased from a hosting provider offers the spammer several advantages. First, zombies cost nothing; the spammer can even use the same machines that he is using to relay spam as supplementary webservers. Secondly, it reduces the spammer's points of contact; renting a virtual host from a hosting company is a business transaction that could possibly lead investigators to the spammer. Thirdly, it may protect the spammer against SURBL-style filtering, which checks URIs in messages to see if the domain referenced resolves to a known spammer IP. Finally, it makes it much harder to close down the spammer's site. There's no hosting provider to shut down the virtual host, and unlike a typical website, which can be rendered inaccessible by taking down a couple of nameservers, a hosting botnet has multiple redundant nameservers that cannot be shut down without the cooperation of each ISP hosting the zombie.
Disadvantages[]
In practice, botnet hosting seems to be of limited effectiveness. Botnet-hosted sites are typically very slow and hard to access. Part of the problem is that zombies are usually domestic PCs using dynamically-allocated IP addresses. Home users often shut their machines down for hours at a time. When a machine shuts down or disconnects, it will often be given a different dynamic IP address when it reconnects and the original IP address may be either unused or assigned to a machine that is not compromised. If the zombie's peers in the botnet are still directing requests to the old IP address, then those requests will fail and the spam recipient will not be able to access the spammer's website, resulting in a lost sale.
Observed in the wild[]
Botnet hosting appears to be popular with spammers who are engaged in particularly illegal activities. For instance, some scammers running job offer scams use botnet hosting for their bait sites. Botnet hosting of embedded images used in stock spam has also been observed.
Botnet Geography Charts[]
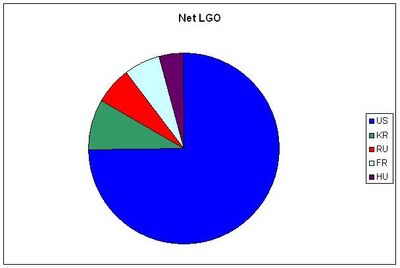
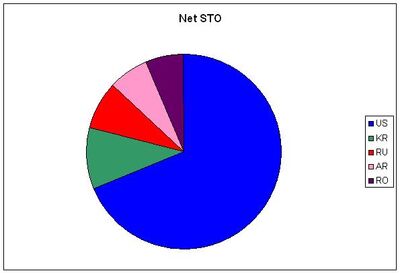
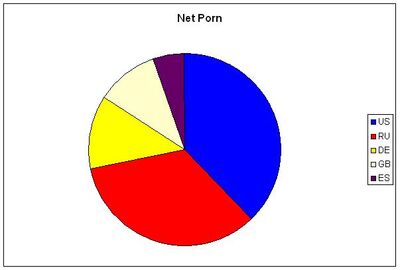
Nine detected botnets are shown in the pie-charts below. In the following table, the spam brands using those botnets are identified. Finally, some DDoS attack botnets are shown for comparison purposes.
The aim of these charts is to provide a fingerprint of the botnets to detect relationships and non-relationships between one botnet and another.
| Botnet Geography | Botnet Geography |
|---|---|
|
|
|

|
| Brand = Anatrim, Piracy | Brand = Pharmacies |
| Brand = Gambling Casino | 
|

|

|

|

|

|
| Botnet Geography | Botnet Geography |
|---|---|
| Net LGO - Reliable Pharmacy, Pharma Shop, Elite Herbal/Herbal King,
SwissWatchesDirect, Wondercum, Naturalism Hoodia/Hoodia Gordonii |
Net STO - Storm malware distribution |
| Net PORN - Porn sites | Net CHE - Prestige Replicas, Diamond Swiss, US Healthcare |
| Net PUF - Anatrim, Penis Enlarge Patch, Canadian Pharmacy, Soft Eden software piracy | Net TAD - Premier Pharmacy, Health Nation, Your Online Pharmacy |
| Net ROY - Gambling Casinos | Net MAR - Money Mule and bank phishing sites |
| DDoS AA - DDoS attack against an anti-fraud site | DDoS CC - DDoS attack on CastleCops anti-phishing site |
| DDoS BB - DDoS attack against another anti-fraud site | DDoS DSLR - DDoS attack on DSLReports (March 2008) |
| Warezov - Virus distribution network (Warezov/Stration) |
Although each of these botnets is unique (not sharing IPs with each other), there is a remarkable correlation between the the first two botnets depicted (LGO and STO). Note how distinctively different the MAR botnet is from the rest, suggesting a completely separate operation. Finally, it can be seen that the DDoS attack fingerprints contrast sharply with the botnets hosting (fast-flux) sites.
Further Reading[]
This resource is made available to botnet researchers and law enforcement alike.
Information specific to the Storm botnet is found at the Wiki page for Storm
A description of the botnet tracking, recording, reporting and removal process is at Botnet Reporting
See also: hijacked host for a description of the various techniques for gaining control of bots.